A New #FollowFriday List for the Cybersecurity Community
After years of hiatus, my weekly #FollowFriday list is back. There's no better home for it than CYBR.SEC.Media, because we are building a community.

After years of hiatus, my weekly #FollowFriday list is back. There's no better home for it than CYBR.SEC.Media, because we are building a community.

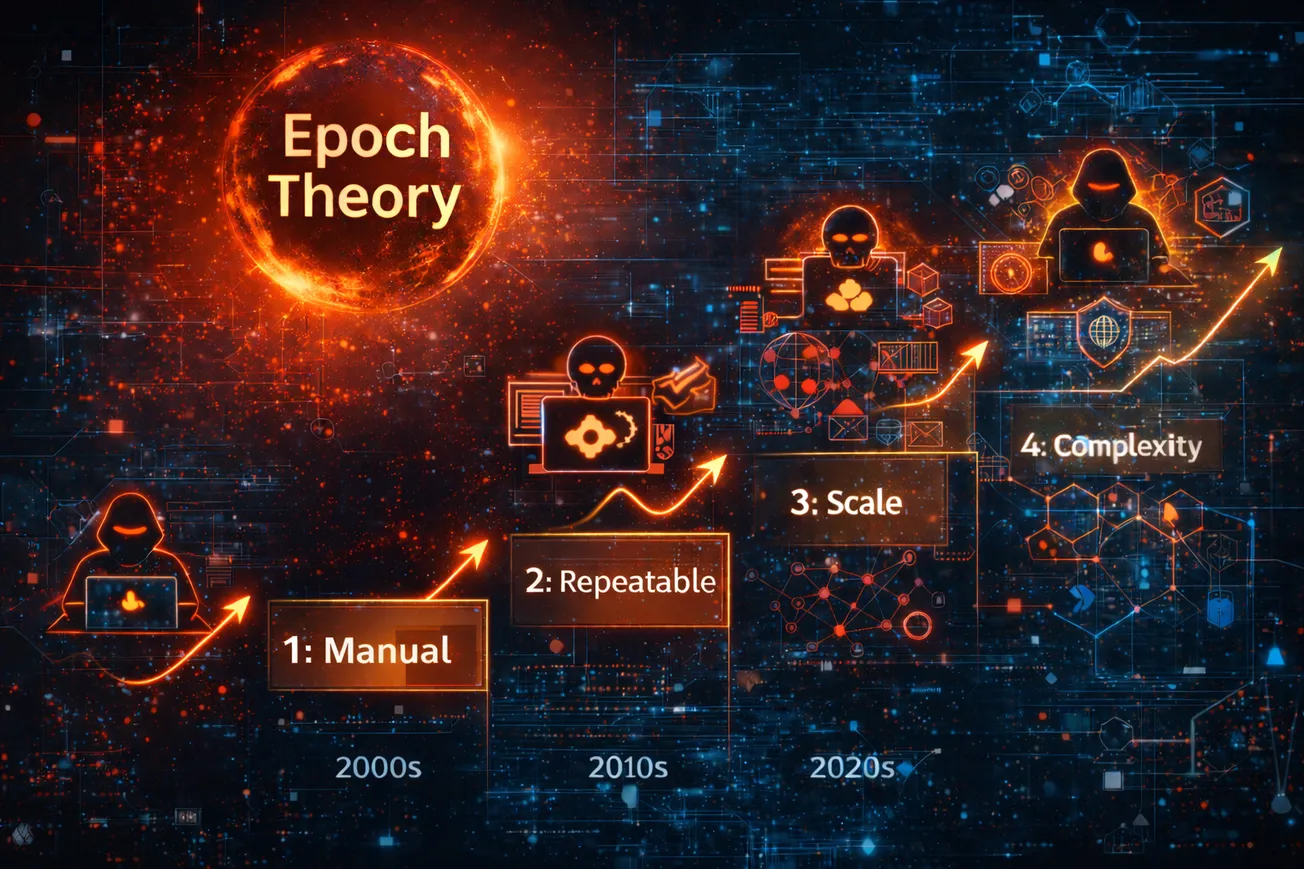
Epoch Theory is Jeremiah Grossman’s framework for understanding how cybersecurity evolves in distinct phases driven by attacker behavior, not defensive intention.


Part of our mission is to be a safe house where cyber travelers can find truth and reason.


AI laws on the books globally, attackers exploiting bad assumptions and bad defaults, the soul-crushing state of the cybersecurity job market, and more!



The world moved swiftly to adopt enterprise AI. Here come the regulations. In this story, we cover what security and risk teams need to know to weather the new regulatory waters.



Many good individuals, nonprofits, and organizations are trying to address this problem in meaningful ways. But too often, those efforts exist in isolation.

For security teams, the message is sobering: initial access brokers such as Gootloader operate at sophisticated technical levels, leverage specialized knowledge of file-format quirks, and maintain operational resilience through rapid innovation.