The pain cybersecurity practitioners feel in the hunt for a job, which we explored a couple weeks ago, spotlighted how employers and job boards (most notably LinkedIn) lean so heavily into AI that job seekers and hiring managers can no longer see each other.

Viewed through a wider aperture, something uglier surfaces: criminal actors hacking other stages on the job recruitment process.
Threat actors linked to North Korea-operated Lazarus Group are targeting developers during the interview process itself, turning technical hiring exercises into malware delivery mechanisms.
ReversingLabs recently detailed a new branch of this operation, dubbed “graphalgo,” which uses fake recruiter campaigns to infect job seekers with a remote access trojan (RAT).
The report captures the architecture of this campaign via the following image:
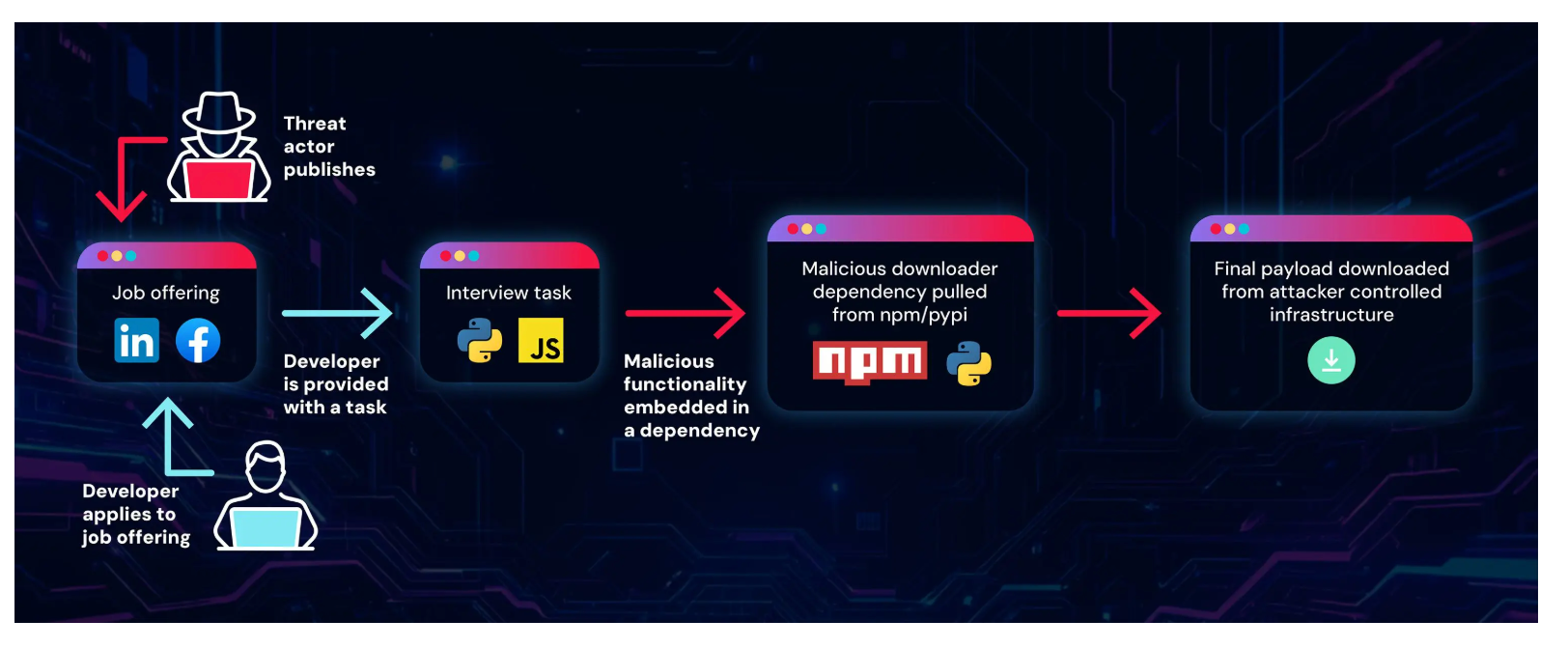
They’re Not Just Pretending to Hire You. They’re Trying to Own Your Machine.
Here is the sequence of events:
1. The attackers create a company – in this case, Veltrix Capital. They register domains early. They seed GitHub repositories. They post on Reddit, LinkedIn, and Facebook. They build recruiter personas. They use AI to generate realistic job descriptions, salary ranges, and regional language.
2. They invite you to a technical interview. You clone a GitHub repository. The code looks normal. The assignment looks plausible. The malware hides in the dependencies.
3. Instead of embedding obvious malicious logic in the visible code, the attackers bury it in NPM and PyPI packages referenced in the project. When your environment installs the dependencies, it installs a RAT.
ReversingLabs reverse engineer Karlo Zanki described the tactic in the report:
“The malicious functionality is not located in the main project files but in the dependencies, which are automatically installed during execution.”
Though cautious developers often review visible code during an interview, few stop to manually inspect every nested dependency in a live technical exercise. That is what the bad guys are counting on.

Precision Targeting
The campaign targets developers with Web3 and cryptocurrency experience. Many of those developers keep browser extensions or local crypto wallets on their machines. Once the RAT installs, it can:
- Enumerate system information
- List processes
- Exfiltrate files
- Search for crypto-related artifacts.
Lazarus has stolen billions in cryptocurrency over the past several years. This campaign aligns with that financial motivation.

Further Down The Spiral
Some malicious packages aren’t immediately weaponized. Attackers publish a benign version first. They build download counts, establish credibility and then push a malicious update.
If your package configuration references "latest", you hand them an auto-update channel.
ReversingLabs observed more than 10,000 downloads tied to packages in this campaign, and it's not limited to developers. In parallel operations, North Korean actors continue to infiltrate companies directly by securing remote roles under fake identities. They collect salaries and steal data. When companies discover the deception, the actors extort them on the way out.
So, ultimately, North Korean hackers are hitting both sides of the hiring process.

When The Interview Is Part of the Threat Model
To avoid becoming a victim of this campaign, ReversingLabs recommended the following:

Matt Johansen summed up the sorry state of affairs in his VulnerableU coverage of the campaign:
“The job market is hard enough right now. You shouldn’t have to worry about getting hacked while trying to get hired. But you do.”